The Ransomware Attack at Colonial Pipeline
Almost half of all U.S. fuel is transported by the Colonial Pipeline, who were a victim of a ransomware attack and forced to cease operation on 8 May, once again spreading tension within businesses who see increasingly frequent attacks.
The Colonial Pipeline announced its breach on 7 May and has since commenced an internal investigation into the impact and the cause of this incident.
What Happened?
As part of a double extortion scheme, hackers stole approximately 100 GB of sensitive data on 6 May, after which they threatened to publish this online. According to Bloomberg, the company proactively shut down certain systems to contain the threat, resulting in a temporary halt to pipeline operations and additional system issues.
Joe Blount, the CEO of Colonial Pipeline, stated on 8 June that he paid hackers a ransom of $4.4 million a day after discovering malware on the company’s systems. To negotiate with the hackers, the company hired outside consultants who made the payment in bitcoin. Shortly following the testimony, the FBI announced it had recovered $2.3 million from the Darkside ransomware.
Colonial Pipeline reported on 10th May that the remediation process is ongoing and that each system is being fixed incrementally.
Vulnerability Disclosure & How Hackers Exploited It?
To this day, it is still unclear how the hackers got access to the internal infrastructure and what were the initial attack vectors. It may have included an older, unpatched vulnerability in the system, a phishing email that enticed an employee within the company, or the discovery and use of valid user credentials by the hackers. There are multiple possibilities, but none of these have yet been confirmed yet.
It should be noted that Darkside targeted the business activities rather than operational systems, suggesting their intention was not just to bring down the pipeline but to make a financial profit by targeting much more sensitive data.
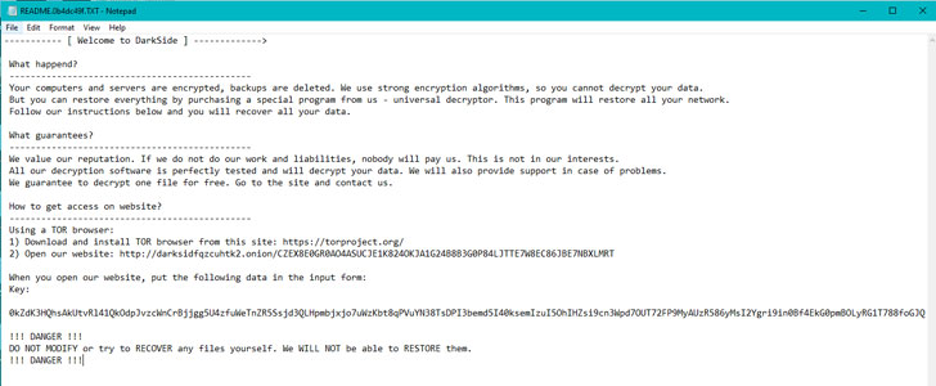
Known as a ransomware-as-a-service (RaaS), Darkside is said to have leaked data related to at least 91 organisations since it began operations in 2020. Partner organisations are recruited to expand the criminal enterprise by infiltrating corporate networks and spreading ransomware, while the core developers are responsible for maintaining malware and payment systems.
The Darkside uses very stealthy methods that are difficult to track, hence there is no definite attack vector found to prove the pathway that they used to target the Colonial Pipeline.
Who was affected?
The attack caused serious damage to the company, but the most affected ones are the consumers. As a result of supply shortage concerns, gasoline futures reached their highest level in three years at the time of the attack. There has been an increase in demand, but drivers are advised not to panic-buy since this could cause prices to rise even further.
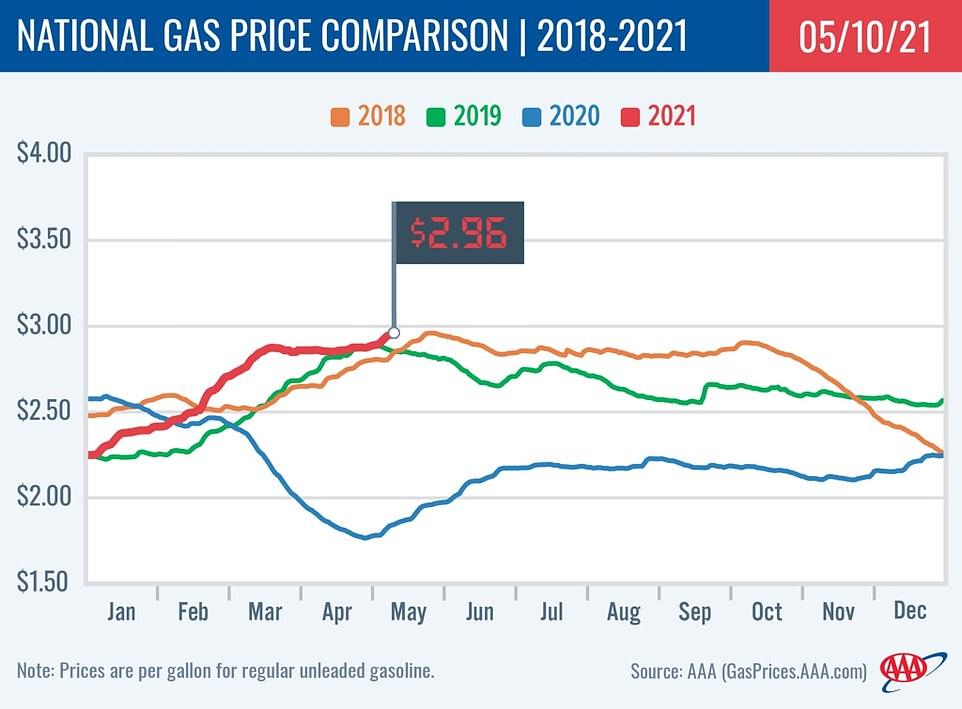
Colonial Pipeline was forced to manage additional lateral supply systems manually with road driven oil tankers, first to those areas that had no fuel delivery service or were experiencing severe shortages.
Conclusion
The Colonial Pipeline ransomware attack was carried out by a hackers group named Darkside who used an unknown initial attack vector to install and spread ransomware within the organisation. The CEO of Colonial Pipelines secretly paid the ransom, but the FBI recovered part of the sent money.