A Primer on The Pegasus Spyware
The most recent event concerning Pegasus Spyware involves Apple. The tech manufacturer has managed to distribute a patch for a critical vulnerability by rolling out security updates in all of its affected iPhones. Since the initial appearance of the malware, Pegasus has had mountainous coverage from international media and governments.
Reports allege that Pegasus spyware is illegally spying on human rights activists, state heads, and journalists through their iPhones. With complete overdependence on the Internet and tech gadgets, the reliance on personal and commercial tasks is no longer safe.
On a global scale, there is a collaborative investigation involving Pegasus spyware. Experts insist that it is one of the most dangerous attacks targeted towards smartphones.
Roots of Pegasus
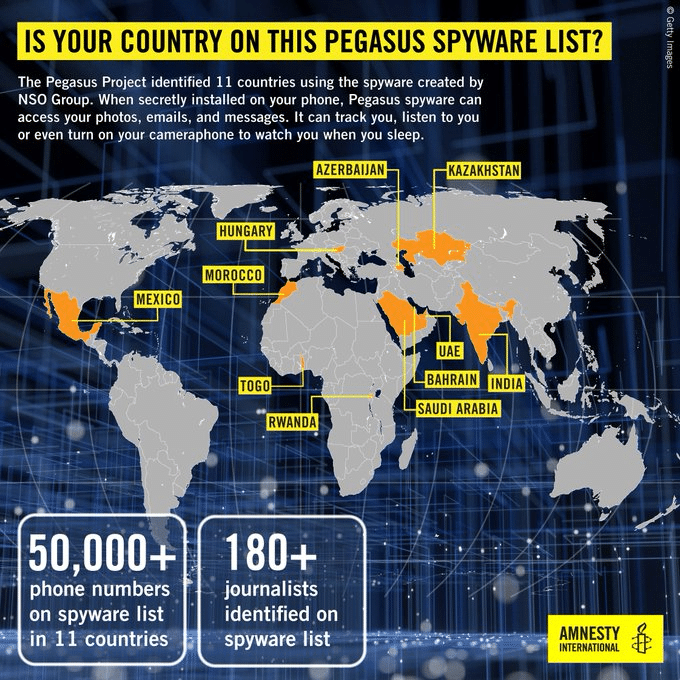
Pegasus is the top-of-the-line spyware of the Israeli NSO Group. The company offers cyber intelligence solutions for state-backed law enforcement and intelligence agencies. The Washington Post confirms that the group offers its services to 60 different governments around the world.
Mechanics of Pegasus
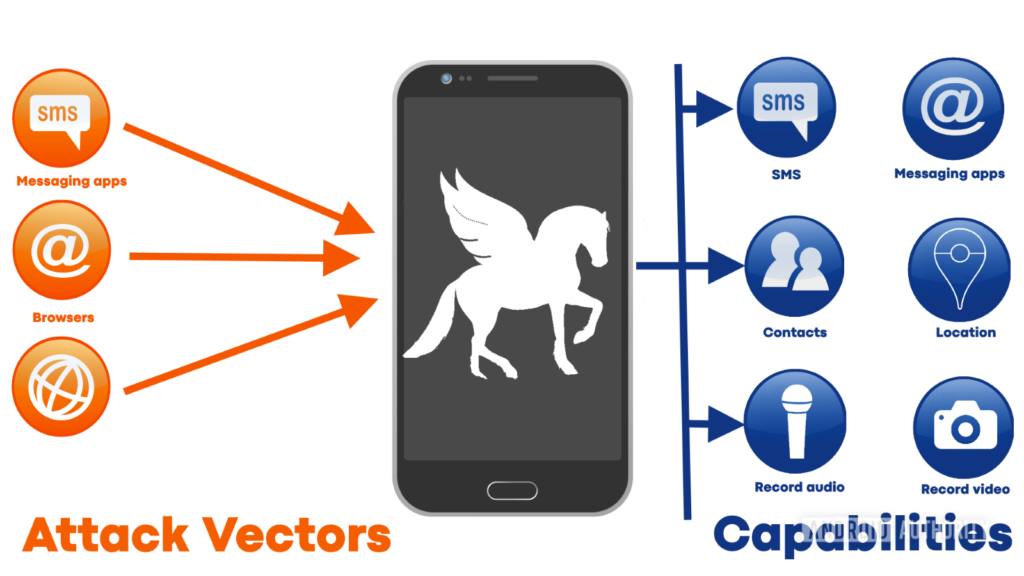
Attackers send an email or text message to a targeted cell phone. Once the victim opens the message or email, the Pegasus Spyware gets access without any need for user interaction (i.e., clicks). The attacker can then download additional modules on the cell phone and transmit surveillance information.
Whether it’s Android or iOS, Pegasus Spyware does not require a click to get be executed. It appears the spyware can infiltrate any type of phone from any location. Once the attacker gets remote access to the phone, it can activate virtual surveillance.
Ultimately, Pegasus Spyware focuses on zero-day vulnerabilities. It is a vulnerability in the operating system of the smartphone that either hasn’t been fixed by the vendor or the user has not updated the device to apply the patches. In a span of few months, Pegasus Spyware has managed to exploit and backdoor millions of iPhones. At the of writing, Apple wants to roll out continuous updates in the software to avoid future attacks.
What Exactly Pegasus Can DO?
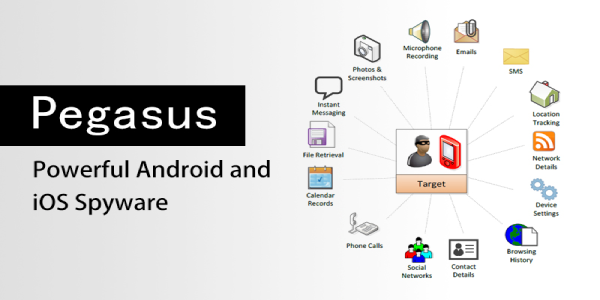
Once the spyware gets into the smartphone, there is practically nothing users can do to stop it. In particular, the attack can see all the photos, videos, emails, contact lists, SMSs, and call records. The attacker can put a GPS tracker on the phone to see the target movements.
Reports also confirm that Pegasus spyware can activate the camera and microphone on the phone. In layman’s terms, it turns a cell phone into a surveillance tool. In the case of iPhones, attackers used Pegasus spyware to obtain administrative or root privileges. After that, it can do everything the owner can on the device.
Targeted Software
In the last two years, there has been a dramatic increase in malware attacks on different types of devices. Pegasus spyware uses a new infiltration technique that doesn’t require clicks or depend on pre-installed (vulnerable) software. It can exploit a smartphone without users’ knowledge.
Final Thoughts
I In late 2021, more details continue to startle tech experts about Pegasus spyware. Tech experts profess that the spyware is (almost) impossible to identify. Despite modern protections and the use of advanced electronic devices, Pegasus spyware leaves no trace of infiltration whatsoever. The new versions of the spyware, however, use the smartphone’s temporary memory.
So, when users switch off their phones, any virtual trace of the spyware infiltration is completely gone. In retrospect, before leading cybersecurity specialists figure out how to detect the spyware, it is crucial to offer support to users who may be victims of this particular malware.